PDF) Spyduino: Arduino as a HID exploiting the BadUSB vulnerability | Vagelis Karystinos - Academia.edu
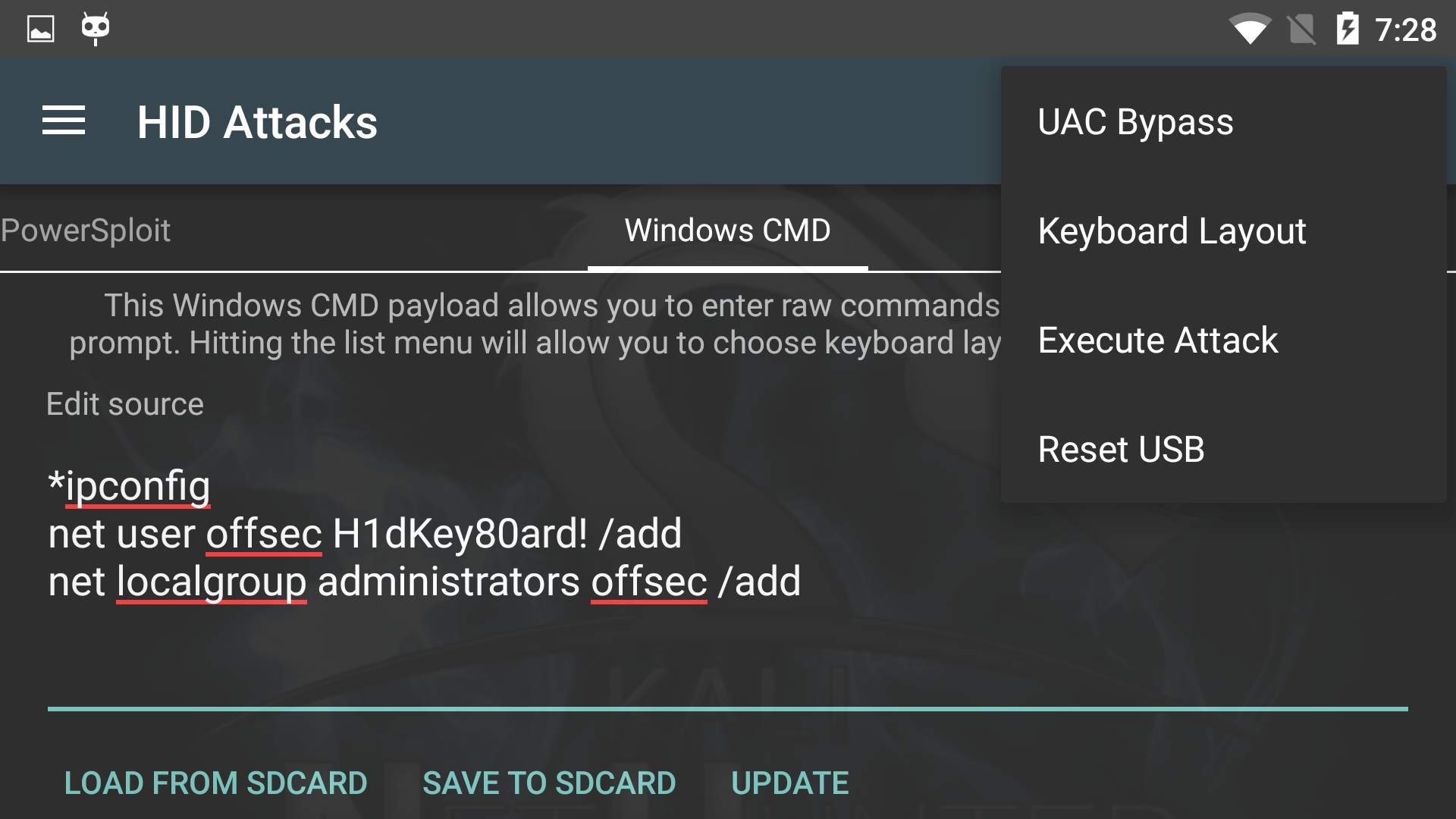
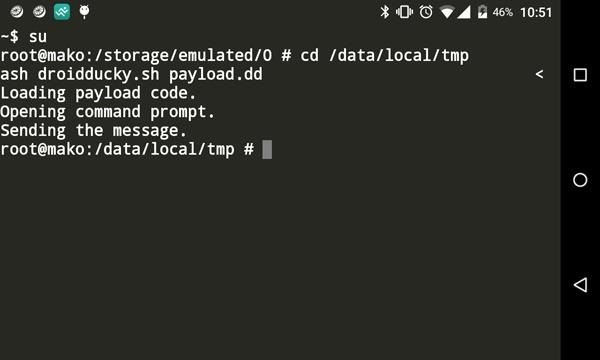
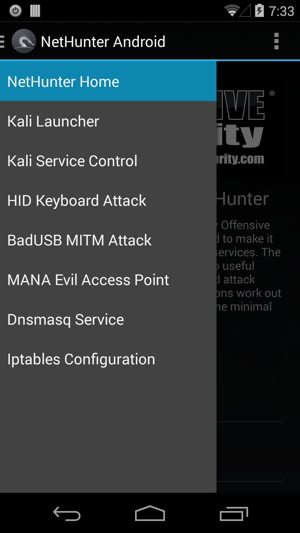
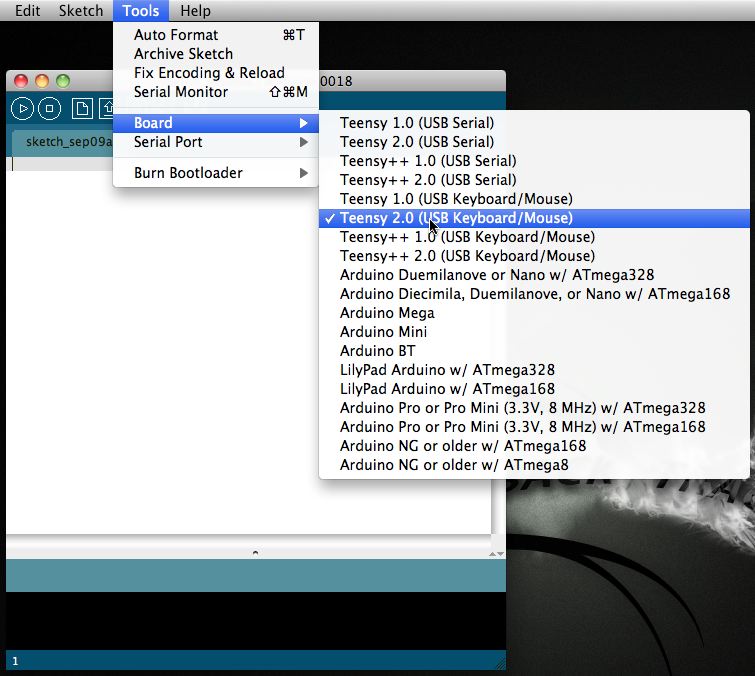
USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium

USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium

Ben S on Twitter: "Its compatible with any regular keyboard. Connects to a PC and looks like a regular HID keyboard. It uses man-in-the-middle attack and decodes the keyboards button presses from the real keyboard, then toggles caps lock on and off after ...
GitHub - samyk/usbdriveby: USBdriveby exploits the trust of USB devices by emulating an HID keyboard and mouse, installing a cross-platform firewall-evading backdoor, and rerouting DNS within seconds of plugging it in.

USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium